Exploiter Series: Sociocultural Exploitation of Bangladesh
Dr. Marcus Griffin
Distribution A: Approved for public release
File Size:
6.23 MB
File Type:
Page Count:
12
Share & Get The Message Out
This analysis, based on the Exploitable Conditions Framework (ECF), examines the systemic vulnerabilities in Bangladesh that allow state and non-state actors to advance their strategic interests and disrupt regional stability.
Key Vulnerabilities & Exploitative Actors:
• Systemic Corruption: Widespread corruption at all levels of government creates opportunities for external actors to exert influence.
• Chinese Influence: China leverages geographic proximity and debt connections (currently 6% of Bangladesh’s external debt) to exert coercive influence over Bangladeshi leaders, particularly regarding infrastructure development.
• Political Instability and Radicalization: Governance shortfalls, economic instability, and political rivalries create conditions ripe for social unrest and radicalization by groups like Jamaat-e-Islami, Hefazat-e-Islam, al-Qaeda in the Indian Subcontinent, and ISIS-K.
• Economic Dependency: Exploitative labor practices in the ready-made garment (RMG) sector and reliance on overseas worker remittances, coupled with reduced foreign direct investment, increase vulnerability to China’s economic coercion.
• Humanitarian Crises and Resource Strain: Environmental shocks exacerbate governance strain, creating opportunities for China and Islamist charities to offer conditional aid and expand their influence.
Implications for Security:
These vulnerabilities pose risks to U.S., Allied, and partner interests, potentially impacting basing or overflight corridors during contingency operations. Understanding these dynamics is crucial for developing effective strategies to mitigate exploitation and enhance regional security.
Related Products
FY 2025 Operational Environment Running Estimate
How Russia Fights in Large-Scale Combat Operations
T2COM OE Threat Assessment 1-1, How China Fights in Large-Scale Combat Operations
Differences in Russian Military Planning Underscore Importance of “Thinking Red”
China’s People’s Liberation Army Heavy Infantry Company Attack on a Fortified Enemy Threat Template
North Korea’s Ukraine War Involvement Signals Escalating Cooperation Among U.S. Adversaries
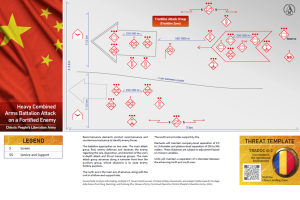
China’s People’s Liberation Army Heavy Combined Arms Brigade Attack on a Fortified Enemy Threat