Complete Archive
Articles in this release include: China China’s 82nd Group Army Brigade Enhances Red-Blue Training To Improve Combat Readiness Chinese Victory…
Articles in this release include: China China’s Army Newspaper Stresses Loyalty to Political Party Chinese Exercise Featuring “Robot Wolves”…
This periodic report assesses the contours of the emerging alliance of the United States’ four primary adversaries: China, Russia, Iran,…
China’s UAS Revolution Advances From Prototype to Practical Application Peter Wood and Jared Kite China’s People’s Liberation Army (PLA) is…
Chinese People’s Liberation Army (PLA) Army political officers play a significant role in the command and control (C2) of PLA…
This template outlines a PLA heavy combined arms battalion employing a positional defense to enhance situational awareness and defensive capabilities.…
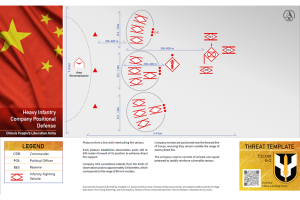
This template outlines a PLA heavy infantry company employing a positional defense. Tactical Formation and Structure: Platoon Alignment: The company is…
China employs warfighting approaches centered on achieving information dominance, disaggregating the U.S. Joint Force, and exploiting strengths in sense, strike,…
T2COM, Directorate of Intelligence and Security (G-2), is producing this Fiscal Year 2025 (FY25) Operational Environment (OE) Running Estimate to…
This paper is the first in a series that builds upon the work presented in T2COM Pamphlet 525-92, The Operational…